-
Inspiracje
- Najnowsze
- Najpopularniejsze
- Zaskocz mnie
- Obserwowane
- MAGazyn
- Moda damska
- DIY - zrób to sam
- Kuchnia
- Uroda
- Wnętrza
- Humor
- Ogród
- Ślub
- Architektura
- Biżuteria
- Design
- Dziecko
- Film
- Fotografia
- Gadżety
- Historia
- Hobby
- Inne
- Książka
- Moda męska
- Muzyka
- Nauka i natura
- Plakaty i obrazy
- Podróże i miejsca
- Samochody i motocykle
- Sport i fitness
- Święta i uroczystości
- Tatuaż
- Zwierzęta
- Partnerzy
- KONKURS
-
Zakupy
-
ONA
- Ubrania
- Bielizna
- Bluzki
- Bluzy
- Dresy damskie
- Kombinezony
- Koszule
- Koszulki
- Kurtki
- Płaszcze
- Spodnie i leginsy
- Spodnie jeans
- Spódnice
- Stroje kąpielowe
- Sukienki i tuniki
- Swetry
- Szorty
- Zestawy
- Żakiety i kamizelki
- Buty
- Baleriny
- Botki
- Czółenka
- Espadryle
- Glany
- Japonki
- Kalosze
- Klapki
- Koturny
- Kowbojki
- Kozaki
- Obuwie Domowe
- Półbuty
- Sandały
- Sportowe i lifestyle
- Szpilki
- Tenisówki i Trampki
- Trapery i trekkingi
- Dodatki
- Bransoletki i zawieszki
- Breloki
- Czapki i kapelusze
- Etui
- Kolczyki, nausznice
- Kołnierzyki
- Kosmetyczki
- Naszyjniki, kolie i zawieszki
- Okulary
- Ozdoby do włosów
- Parasole
- Paski
- Pierścionki
- Plecaki
- Portfele
- Rękawiczki
- Skarpety
- Szaliki i chusty
- Torby i torebki
- Walizki
- Zegarki
- Zestawy biżuterii
- Zdrowie i uroda
- Balsamy
- Bazy i podkłady
- Cienie do oczu
- Dezodoranty
- Higiena jamy ustnej
- Korektory
- Kredki
- Kremy i serum
- Lakiery
- Manicure i pedicure
- Maseczki
- Odżywki
- Peeling
- Perfumy i wody perfumowane
- Pielęgnacja po opalaniu
- Płyny żele i mydła
- Pomadki i błyszczyki
- Pudry
- Róże
- Stylizacja włosów
- Szampony
- Toniki i demakijaż
- Tusze
- Wody toaletowe
- Zestawy
-
ON
- Ubrania
- Bielizna
- Bluzy
- Kąpielówki
- Koszule
- Kurtki i płaszcze
- Marynarki kamizeki
- Spodenki i szorty
- Spodnie
- Swetry
- T-shirt długi rękaw
- T-shirt i Polo
- KULTURA
- GADŻETY
- DZIECKO
-
DOM I WNĘTRZE
- Wnętrza
- Akcesoria dom
- Ceramika i szkło
- Do baru
- Do biura
- Do kuchni
- Kubki kufle i kieliszki
- Lustra
- Nakrycia stołu
- Oświetlenie
- Plakaty i tablice
- Pościele, poduszki i nakrycia
- Przechowywanie
- Tekstylia
- Zegary i budziki
-
Marki
- MARKI
- Adidas
- Adriatica
- Alter Core
- Armani
- Asics
- Atlantic
- Azzaro
- Barbie
- Bburago
- Be-U
- Benetton
- Bering
- Black Plum
- Burberry
- Bvlgari
- Cacharel
- Calvin Klein
- Canon
- Carolina Herrera
- Carrera
- Casio
- Celestron
- Chanel
- Chloe
- Clinique
- Cobi
- Coloud
- Converse
- David Beckham
- Davidoff
- Delbana
- Diesel
- Dior
- DISNEY
- DKNY
- Dolce & Gabbana
- DOXA
- Dr. Martens
- Dunhill
- Ecco
- Elizabeth Arden
- Esprit
- EVC DSGN
- Festina
- Fila
- Fisher Price
- Frederique Constant
- Givenchy
- Gucci
- Guerlain
- Guess
- Hasbro
- Helena Rubinstein
- Hermes
- Hi-Tec
- Hugo Boss
- Hunter
- Iceberg
- Ingersoll
- Issey Miyake
- Jean Paul Gaultier
- Jennifer Lopez
- Jil Sander
- Jimmy Choo
- Joop!
- Juicy Couture
- Kappa
- Kenzo
- Komono
- Lacoste
- Lalique
- Lancome
- Lanvin
- Lee
- Lego
- Lorus
- Marc Jacobs
- Marshall
- Masaki Matsushima
- Matchbox
- Mattel
- Max Factor
- Max&Co
- Mc Arthur
- Mizuno
- Mont Blanc
- Moschino
- Mr. Gugu & Miss Go
- My Little Pony
- New Balance
- Nike
- Nikon
- Nina Ricci
- Ninety Eight Clothing
- Nivea
- Nixon
- Nooka
- Obaku
- Onitsuka Tiger
- Paco Rabanne
- Pentax
- Pewex
- Pierre Cardin
- Playboy
- Prada
- Puma
- Ralph Lauren
- Reebok
- Regatta
- Revlon
- Rexona
- Rider
- Salomon
- Salvatore Ferragamo
- Shelyak
- Shiseido
- Skagen
- Swarovski
- Takahashi
- Thierry Mugler
- Timberland
- Timex
- Tommy Hilfiger
- UGC
- Urbanears
- Valentino
- Vans
- Versace
- Viktor & Rolf
- Vixen
- Welly
- William Optics
- Wrangler
- Yimaida
- Yukon
- Yves Saint Laurent
-
ONA
-
Szukaj
- Losuj
Hobby
Unicorn Ultra
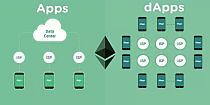
Public Key and Private Key - Understanding the Key Components of Cryptographic Security
>>> https://uniultra.xyz/blog/public-key-and-private-key
In the world of cryptography, public key and private key play a pivotal position in making sure comfy communication and transactions. These cryptographic keys form the inspiration of various present day safety protocols and are essential to the functioning of technologies consisting of blockchain and virtual signatures. In this blog publish, we can delve into the sector of public key and private key, exploring their definitions, variations, and the vital roles they play in safeguarding sensitive facts.
Understanding Public Key Cryptography
Public key cryptography, also referred to as uneven cryptography, is a essential idea in modern-day cryptography. At its core, public key cryptography makes use of a pair of keys - public key and private key - to encrypt and decrypt facts. The public key's openly shared, at the same time as the private key's stored secret. The primary reason of the public secret's to encrypt facts, even as the private secret's used for decryption.
What is Private Key?
A non-public key's an critical thing in public-key cryptography, a cryptographic system that is predicated on pairs of keys for at ease conversation and information encryption. In this system, the non-public secret is a unique, mystery piece of statistics that is acknowledged solely to the proprietor. It plays a critical position in two important operations: decryption and virtual signing.
When it comes to decryption, the private secret's used to unencumber encrypted messages or information which have been encoded using the corresponding public key. This manner guarantees that only the intended recipient, who possesses the non-public key, can get right of entry to and decipher the encrypted facts.
Additionally, the non-public secret's used for virtual signing, which entails attaching a completely unique digital signature to a message or record. This signature offers a means of verifying the authenticity and integrity of the content. By the use of their non-public key, the sender can create a signature that can be demonstrated through anybody with get entry to to the corresponding public key. This lets in recipients to affirm that the message or report originated from the anticipated sender and that it hasn't been altered in transit.
Key Differences and Use Cases between public key and private key
Public and personal keys fluctuate of their functionality and utilization. Public keys are designed for encryption, allowing comfortable communication among parties. They are commonly used in comfortable protocols inclusive of SSL/TLS for securing net connections. Private keys, on the other hand, are used for decryption and digital signatures, allowing identification verification and ensuring records integrity. Private keys are vital in technology like cryptocurrency wallets, in which they are used to authorize transactions and offer possession evidence.
Follow https://uniultra.xyz/ for more blockchain updates.
>>> https://uniultra.xyz/blog/public-key-and-private-key
In the world of cryptography, public key and private key play a pivotal position in making sure comfy communication and transactions. These cryptographic keys form the inspiration of various present day safety protocols and are essential to the functioning of technologies consisting of blockchain and virtual signatures. In this blog publish, we can delve into the sector of public key and private key, exploring their definitions, variations, and the vital roles they play in safeguarding sensitive facts.
Understanding Public Key Cryptography
Public key cryptography, also referred to as uneven cryptography, is a essential idea in modern-day cryptography. At its core, public key cryptography makes use of a pair of keys - public key and private key - to encrypt and decrypt facts. The public key's openly shared, at the same time as the private key's stored secret. The primary reason of the public secret's to encrypt facts, even as the private secret's used for decryption.
What is Private Key?
A non-public key's an critical thing in public-key cryptography, a cryptographic system that is predicated on pairs of keys for at ease conversation and information encryption. In this system, the non-public secret is a unique, mystery piece of statistics that is acknowledged solely to the proprietor. It plays a critical position in two important operations: decryption and virtual signing.
When it comes to decryption, the private secret's used to unencumber encrypted messages or information which have been encoded using the corresponding public key. This manner guarantees that only the intended recipient, who possesses the non-public key, can get right of entry to and decipher the encrypted facts.
Additionally, the non-public secret's used for virtual signing, which entails attaching a completely unique digital signature to a message or record. This signature offers a means of verifying the authenticity and integrity of the content. By the use of their non-public key, the sender can create a signature that can be demonstrated through anybody with get entry to to the corresponding public key. This lets in recipients to affirm that the message or report originated from the anticipated sender and that it hasn't been altered in transit.
Key Differences and Use Cases between public key and private key
Public and personal keys fluctuate of their functionality and utilization. Public keys are designed for encryption, allowing comfortable communication among parties. They are commonly used in comfortable protocols inclusive of SSL/TLS for securing net connections. Private keys, on the other hand, are used for decryption and digital signatures, allowing identification verification and ensuring records integrity. Private keys are vital in technology like cryptocurrency wallets, in which they are used to authorize transactions and offer possession evidence.
Follow https://uniultra.xyz/ for more blockchain updates.
MA==
Podobne inspiracje
U2U - The Revolutionary Platform Combining Blockchain a…
Utilize U2U Wallet to talk with properly remarkable ski…
What is Layer 1 blockchain? Types of Layer 1 blockchain…
Unleash crowdsourcing with blockchain era - Unicorn Ult…
Network, Connect, Learn: Unicorn Ultra's Exclusive…
What is a Venture Builder? How does Venture Builder ran…
Venture Builder model - Opportunities for startups with…
What Is a Web3 NFT Marketplace? Exploring the Future of…
What is an NFT Marketplace? How does an NFT Marketplace…
What Is a Blockchain? Understanding the Basics of this…
What Is a Blockchain Platform? Exploring the Basics and…
What is a Dapp? Understanding Decentralized Application…
Beginner’s Guide to dApps - What are differences betwee…
How to Buy NFTs: A Beginner's Guide to Purchasing…
How to Protect Yourself from NFT Scams?
>>> h…
What is cryptocurrency? Tips to invest in cryptocurrenc…
What Is DeFi? A Comprehensive Guide to Decentralized Fi…
What Are DeFi Wallets and How Do They Work?
>>&g…
DeFi vs CeFi: Comparing Decentralized to Centralized Fi…
What are Blockchain Protocols? How Does Blockchain Prot…
What Is a Private Key and Why Is It Important for Your…
UNI-ASTRO: A JOURNEY TO EXPLORE PROMISING VALUES OF U2U…
What is STO? Why will this form of capital soon become…
Top Benefits of Investing in Cryptocurrencies - Should…
What is a blockchain Layer-1 and Layer-2? Difference be…
Applications of Blockchain - What You Need to Know
App…
Compilation of Unicorn Ultra's notable monthly rec…
Unicorn Ultra's May Monthly Recap: Notable Highlig…
How to get U2U testnet coin
>>> https://uniul…
How to use U2U Wallet for storing digital assets and ac…
What is a crypto wallet? What to consider when picking…
How to mint UniAstro NFT with U2U Wallet?
>>>…
What is an NFT? An unlimited potential application of t…
How to Buy and Sell NFTs on U2NFT
>>> https:/…
What is FOMO? Fear of Missing Out
>>> https:/…
AMA RECAP: UNICORN ULTRA X CRYPTO TALKZ
>>> h…
What's the crypto shark and its influence on the m…
How to Transfer NFTs on U2U Wallet? Comprehensive Guide…
Web2 vs Web3 - Exploring the Next Evolution of the Inte…
Hot Wallet and Cold Wallet - Choosing the Right Solutio…